Configuring Azure AD authentication
Contents
- Registering and configuring an application in Microsoft Azure Active Directory
- Configuring Microsoft Azure Active Directory authentication in CMW Tracker
Registering and configuring an application in Microsoft Azure Active Directory
Registering an application in Microsoft Azure Active Directory
In order to register an application in Microsoft Azure Active Directory , you need to go to the “ Azure Active Directory ” settings under your account at portal.azure.com . You need to go to the “ App registrations ” section and then click on “ New registration ”. Give your new application a name (“CMW Tracker” would be a good, self-explanatory name), and specify your CMW Tracker instance’s URI in the corresponding box.
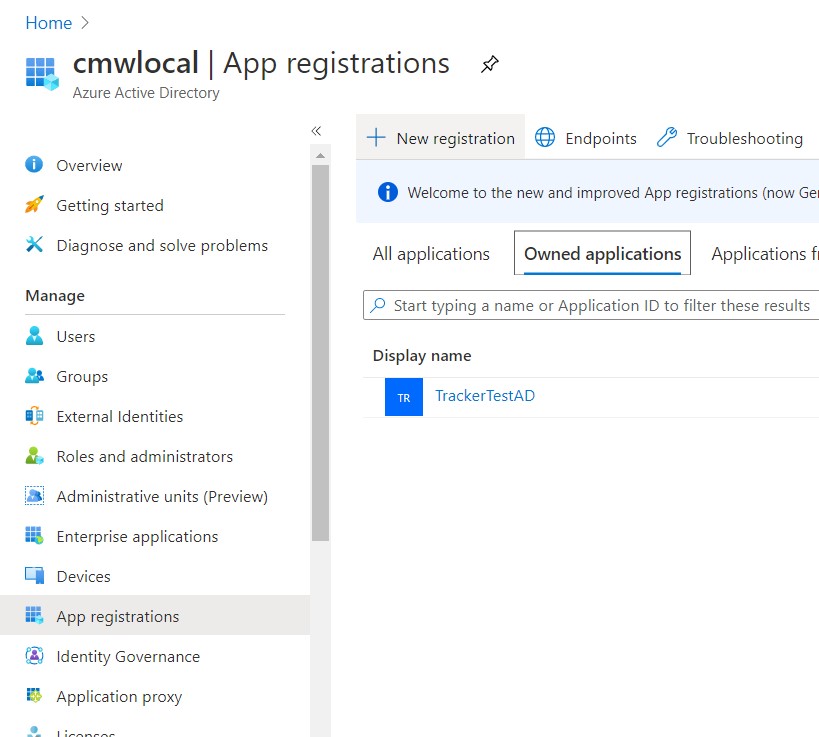
Registered application in Azure Active Directory settings
Configuring a registered application in Microsoft Azure Active Directory
After registering an application in Microsoft Azure Active Directory, you need to open the “Authentication” section of the registered application’s settings. The URIs you need to specify under “Web” -> “Redirect URIs” and “Logout URL” in this section are the web pages users will be redirected to after logging in and after logging out, accordingly. To retrieve those URIs, go to the Administration area of your CMW Tracker, open “Azure Active Directory authentication”, copy URIs from “Redirect URI” and “Logout URI” fields and paste them in the respective fields in the application. After doing that, you also need to check the “ID tokens” option under the “Implicit grant” tab.
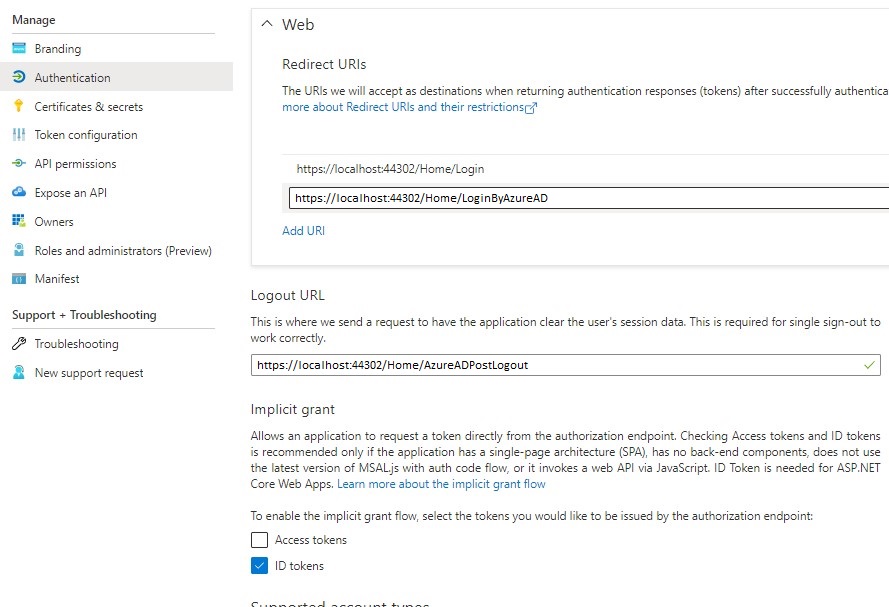
Authentication section
As the next step, you need to configure the authentication token to include the users’ email addresses when they log in. To do that, go to the “ Token configuration ” section, then click on “ Add optional claim ”. In the window that pops up, select the “ ID ” token type, check the “ email ” claim and press “ Add ” to add it.
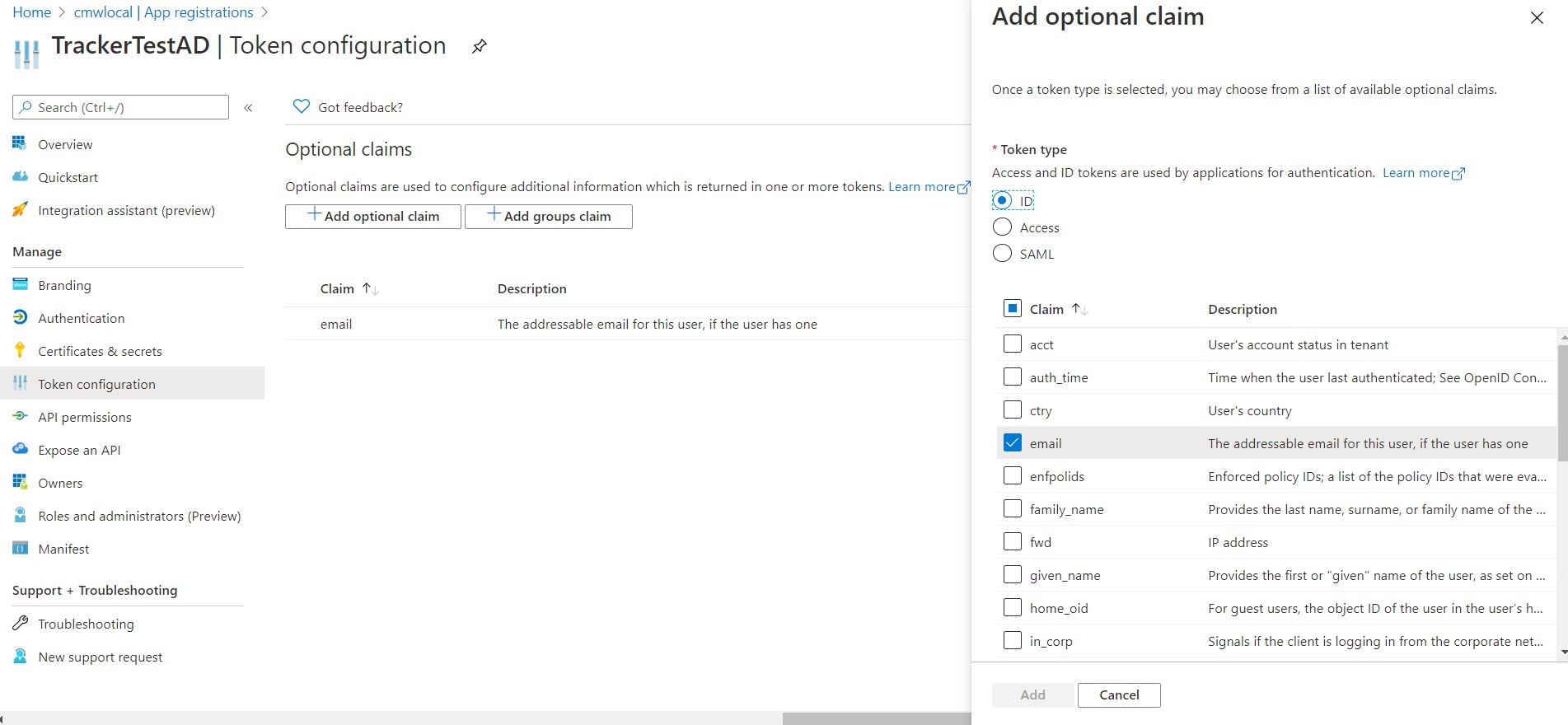
Token settings
User accounts in Microsoft Azure Active Directory
You need to make sure relevant user accounts are added to the Microsoft Azure user catalogue intended for authentication using OpenId Connect . This can be done under the “ Users ” section of Microsoft Azure Active Directory settings. On that page you can either import user accounts or create them manually. Keep in mind that the email addresses of the accounts you add should be the same as those configured for corresponding user accounts in CMW Tracker.
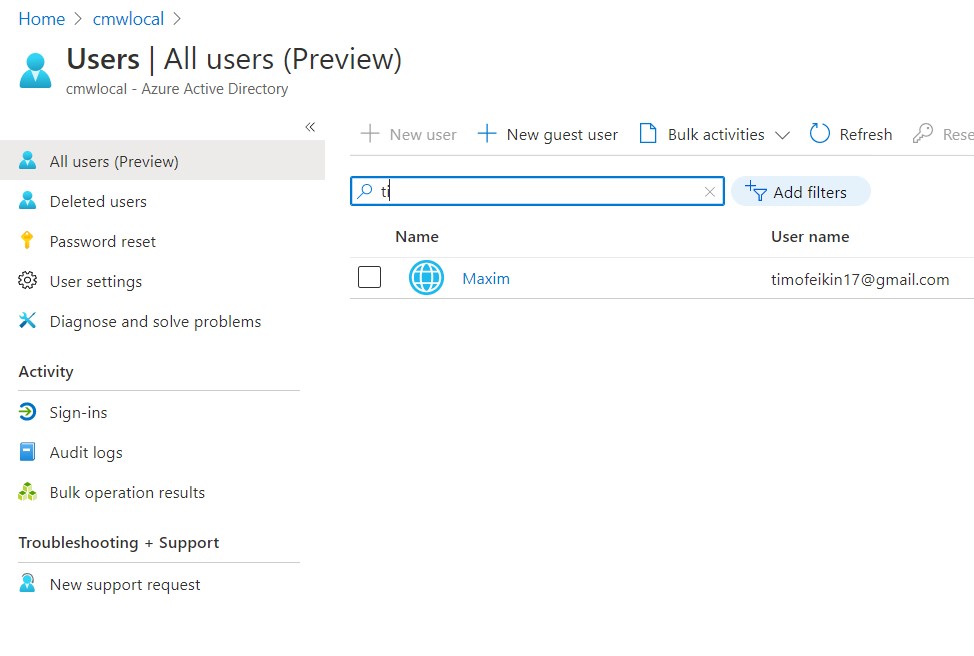
User management in Microsoft Azure Active Directory
Configuring Microsoft Azure Active Directory authentication in CMW Tracker
General settings
To configure user authentication via Microsoft Azure Active Directory in CMW Tracker, you need to go to the Administration area and open the “ Azure Active Directory authentication ” tab. Here is an outline of the settings you can find there:
- Enable authentication – activate/deactivate OpenId Connect (if disabled, users won’t see the button for authenticating with Azure AD at the logon screen);
- Application (client) ID – enter the Application ID of the application you registered in Microsoft Azure Active Directory;
- Directory (tenant) ID – enter the Directory ID of the application you registered in Microsoft Azure Active Directory;
- Redirect URI – this section is generated automatically in the format of: https://{yourhost}/Home/LoginByAzureAD;
- Logout URI - this section is generated automatically in the format of: https://{yourhost}/Home/AzureADPostLogout.
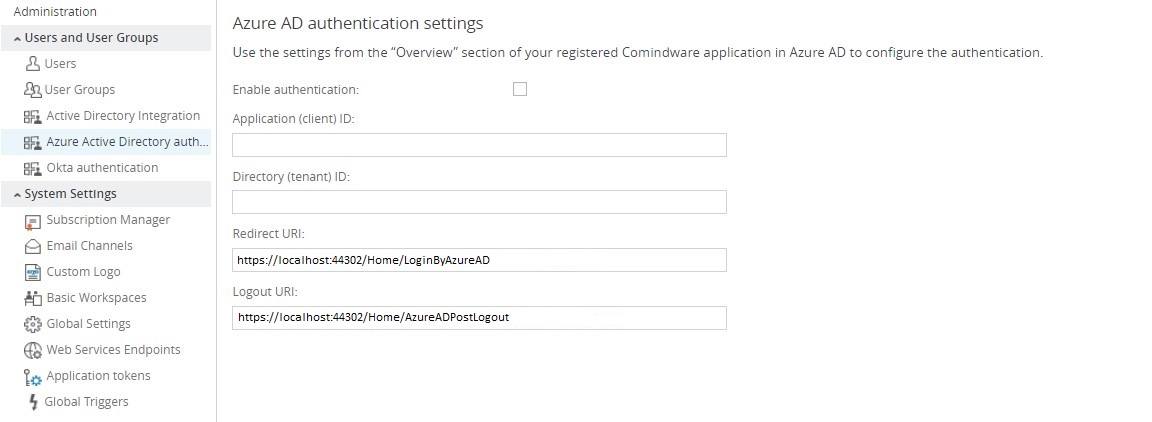
Azure Active Directory authentication settings in CMW Tracker
You can find the Application ID and the Directory ID in the Overview section of the registered application settings at portal.azure.com :
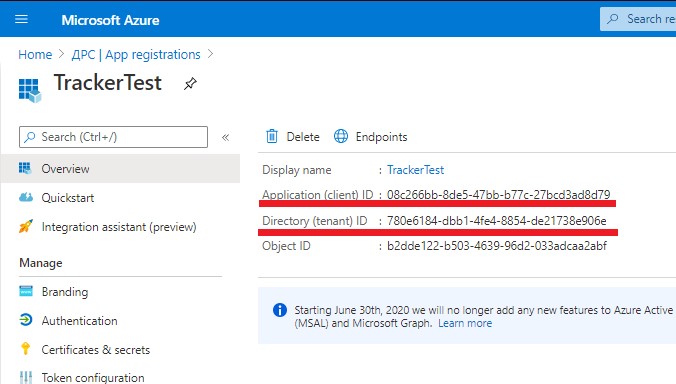
"Overview" section of the application
Configuring user accounts to use Microsoft Azure Active Directory authentication in CMW Tracker
There are four authentication methods used for user accounts in CMW Tracker: local, Active Directory, Azure Active Directory and Okta authentication. Each user account can have just one of them enabled for it at one time. In order to enable the Microsoft Azure Active Directory authentication for a user account, you need to go to the Administration area , then to the Users tab, open the user account settings and pick the corresponding authentication method:
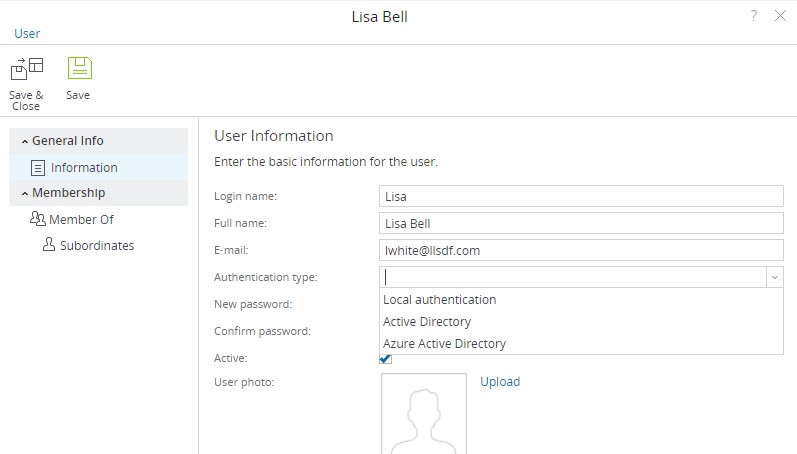
Selecting the authentication method for a user account
